Hi All
We’ve been advised by our IT department that they are planning to decommission the ADFS servers across the organization. They’ve proposed using Azure AD as an alternative.
They’ve supplied me with the documentation here…
Azure Single Sign On SAML Protocol - Microsoft Entra | Microsoft Docs
… can you confirm that Netcall/Liberty Create support this method of configuring SSO, and if so, is there any documentation for setting it up (we’ve previously used https;//community.netcall.com/resources/adfs-as-a-saml-provider/ , but this is specific to ADFS).
Thanks
Stephen
Hi Stephen,
I can confirm Liberty Create can use this type of SSO authentication.
I would advise finding appropriate documentation from your SSO provider and checking the Liberty Create docs for the initial setup.
I would recommend using the OpenID Connect method instead of SAML (if this is available)
Regards
1 Like
Thanks for the feedback.
We’ve managed to get the “Sign On” part of the SSO solution working (Netcall, Azure and SAML 2.0).
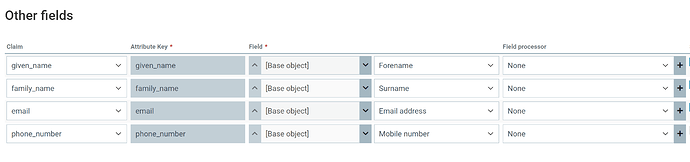
However, it’s not pulling through the additional fields we’ve configured in the attribute mapping (just forename, surname and email address, nothing out of the ordinary).
There’s no errors etc in the detective, the SSO just logs in/creates accounts with just a username (NameID). Both our IT team and myself are at a bit of a loss as to why.
Our IT have suggested…
"is this something we could ask the supplier? It’s probably down to what claims are being passed across but looking through the documentation I can’t see what else to try
this might be useful for them
"
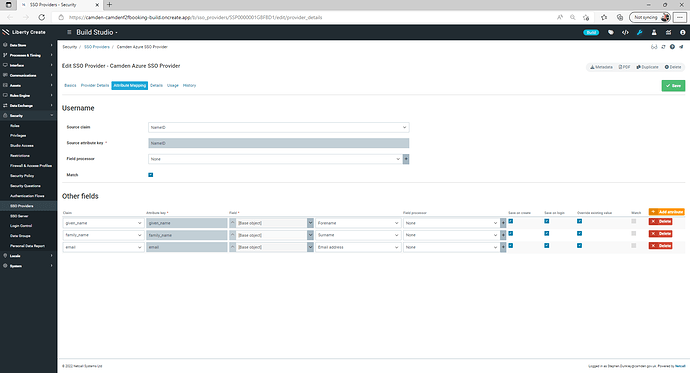
Or attribute mapping is set-up as follows…
Any helps/guidance would be very much appreciated.
Thanks
Stephen
Hi @camsd047,
I’ve just been setting up SSO and have been ripping my hair out over the same issue for the last hour.
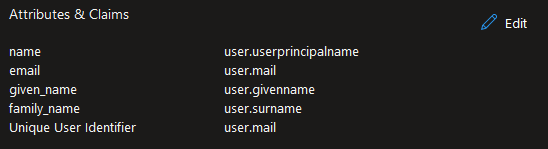
These are the Azure AD attributes: User profile attributes in Azure Active Directory B2C | Microsoft Docs
In your case you’d want 3 custom claims with:
givenName
surname
emailaddress (at least, that’s what it is for us)
Good luck,
Nic
(Bracknell Forest Council)
1 Like
Hi Stephen
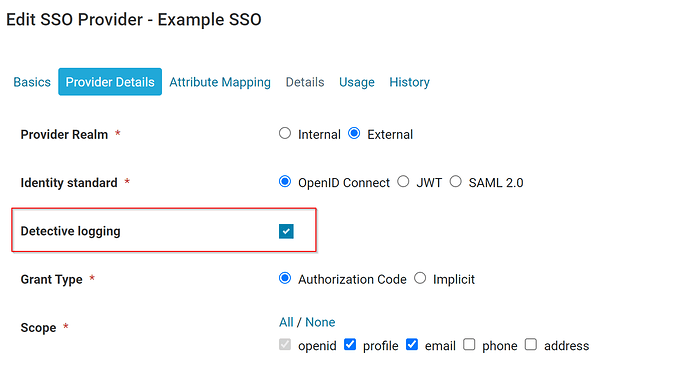
Can I confirm the “Identity standard” you are using is OpenID Connect?
If so, have you tried turning on the “Detective logging” within your SSO provider settings?
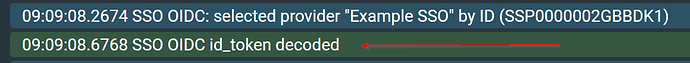
Once this has been enabled, open up “detective” and attempt to login via the SSO with an additional user.
You should see within the logging the following:
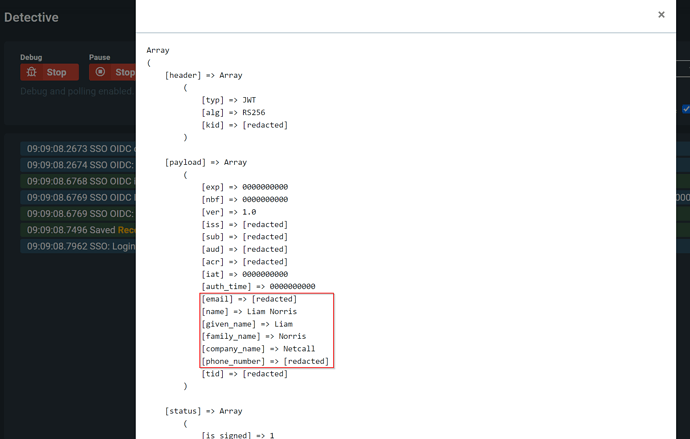
Click on the “SSO OIDC id_token decoded” row, it will open up a popup and display something similar to this:
(Sensitive information has been redacted)
Then within your SSO Provider > Attribute Mapping tab, I would configure the mappings like:
I hope this helps, let me know if you are still facing issues.
Regards
Liam Norris
1 Like
Further to Liam’s advice, if you are using SAML, the details tab also contains the keys of available claims.
Thanks Nic (and everyone else who replied to this thread) - We’ve got it working now using the custom claims you suggested.
1 Like